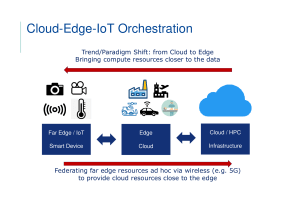
The Internet of Things (IoT) Good morning everyone and welcome to my presentation. First of all, let me thank you all for coming here today. Let me introduce myself. I'm Tymofii Chechil from Sumy State University faculty of Electronics. As you can see on the screen, our topic today is (The Internet of Things) IoT technology. By the end of this presentation you will be familiar with technology which allows you to automate a lot of areas of human activity. I’ve divided my presentation into three main parts, namely IoT concept, aspects to be addressed before adopting a IoT solution and architectural solution that improves the IoT systems. First of all, I'd like to give you a brief overview of what is IoT technology and why is so important. The IoT describes physical objects (or groups of such objects) that are embedded with sensors, processing ability, software, and other technologies that connect and exchange data with other devices and systems over the Internet or other communications networks. Overall, These objects collect data from their surroundings which are then transmitted and remotely analyzed to create new insights, deliver services, and control other items In addition to this, The potential for tremendous growth, innovation, applications, and services is a testament to the open nature of the Internet’s architecture and design, which does not place limits on the kinds of devices or services that can connect to it. Moreover, it is projected that there will be 100 billion connected IoT devices by 2025. Let's now move on to main part of our topic. My first point concerns IoT concept. As mentioned above there are some of the existing technologies which have made it possible to transform a concept of IOT into practice. These are as follows: 1. Low-cost low power sensors: The availability of economic/affordable sensors made it easy for manufacturers to use IoT technology. 2. Network Protocols: There are many network protocols available that allow connection of sensors to the cloud and the other things for data sharing. 3. Cloud Computing: In the current scenario, there are numerous cloud computing platforms available like Amazon AWS, Microsoft Azure, Google Cloud, etc. which enables both consumers and businesses to access the infrastructure as required without any management overhead. 4. Machine Learning: Machine learning is a programming language containing multiple algorithms that are used to extract data, analyze it and then predict future trends based on the developed data. This emerging technology has pushed boundaries for IoT. 5. Artificial Intelligence (AI): Advancement in neural networks has brought digital intelligence to IoT devices. For example, digital personal assistants in mobiles like Alexa, Siri, etc. Next, I’ll focus on aspect to be addressed before adopting a IoT solution. The internet of things offers several benefits to organizations. Some benefits are industry-specific, and some are applicable across multiple industries. Some of the common benefits of IoT enable businesses to: monitor their overall business processes; improve the customer experience (CX save time and money; enhance employee productivity; integrate and adapt business models; make better business decisions; and generate more revenue. as listed in Table on the screen. IoT encourages companies to rethink the ways they approach their businesses and gives them the tools to improve their business strategies. Finally, we will focus on architectural solution that can improve IoT systems. According to the The devices connected to IoT can be secured by implementing active security measures in their software. Providing security measures such as password protection for accessing the software is one of the ways to safeguard devices from threats and potential attacks. Passwords can be in the form of digital codes, static or dynamic, confidential to the user. Another method to provide IoT security is to restrict the use of internet on the connected devices. Blocking a program behind a firewall or restricting usage to only certain features of the software, saving critical data from leaking. All the devices connected to the network should be updated to the latest software. Constant monitoring for potential threats should be put into practice and immediate resolution should be sought for bugs and security loopholes found during an inspection. In conclusion, I would like to summarize all the above. Today we discussed the Internet of Things involves a complex and evolving set of technological, social, and policy considerations which require input from a diverse set of stakeholders. Finding solutions will thus require informed engagement, dialogue, and collaboration across a range of stakeholders to plot the most effective ways forward. Thank you for listening. If you have any questions, I’d be pleased to answer them.